
Proactive Cyber Penetration Testing
In today’s digital landscape, businesses of all sizes are vulnerable to a growing number of sophisticated cyberattacks. The need to secure your network, applications, and data is more critical than ever. Our penetration testing services help you stay one step ahead of attackers by identifying and addressing potential security vulnerabilities before they can be exploited.
Get A Quote
What is Penetration Testing?
Penetration testing (pen testing) is a simulated cyberattack on your network, applications, or systems to evaluate the security of your digital infrastructure. This proactive approach allows security experts to uncover vulnerabilities, misconfigurations, and other weaknesses that malicious hackers could exploit. By replicating real-world attack scenarios, penetration testing helps you safeguard your assets and maintain customer trust.
Our Penetration Testing Services
Our comprehensive penetration testing services cover a wide range of testing types, ensuring that every aspect of your organization’s digital environment is thoroughly assessed for security weaknesses.
-
Network Security
-
Application Security
-
Mobile Application
-
Cloud Security
-
Social Engineering
-
Wireless Network
Network Penetration Testing
We simulate real-world attacks to uncover vulnerabilities in your network infrastructure, ensuring your network is secure from internal and external threats.
- External and internal network security testing.
- Identification of open ports, misconfigurations, and access control weaknesses.
- Detailed recommendations for network hardening.
Web Application Penetration Testing
We identify and fix vulnerabilities like SQL injection and cross-site scripting in your web applications, protecting against common attack vectors.
- In-depth testing of web applications, APIs, and associated services.
- OWASP Top 10 vulnerability assessment.
- Remediation guidance to secure your applications from future attacks.
Mobile Application Penetration Testing
We detect security gaps in your mobile apps, APIs, and communication channels on iOS and Android platforms, safeguarding your sensitive data.
- Testing for mobile-specific vulnerabilities (iOS and Android).
- API security and encryption assessment.
- Data leakage and reverse engineering checks.
Cloud Penetration Testing
We uncover misconfigurations and access control weaknesses in cloud infrastructures like AWS, Google Cloud, and Microsoft Azure to secure your cloud environments.
- Comprehensive testing of cloud configurations, storage, and access controls.
- Evaluation of multi-cloud and hybrid environments.
- Recommendations for cloud security improvements.
Social Engineering Testing
We evaluate your organization's susceptibility to phishing and impersonation attacks, helping strengthen your defenses against social engineering tactics.
- Email phishing simulations.
- Pretexting and impersonation assessments.
- Training recommendations to strengthen your human firewall.
Wireless Network Penetration Testing
We assess your wireless network security to identify vulnerabilities that could lead to unauthorized access, ensuring your wireless infrastructure is secure.
- Assessment of encryption protocols, access points, and rogue devices.
- Testing for WPA2, WPA3, and other wireless security standards.
- Detailed report on wireless network vulnerabilities.
How the Process Works
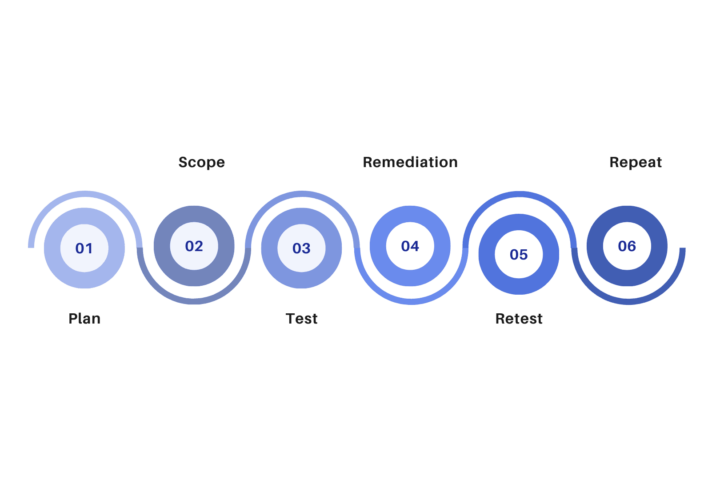






Why Choose Our Penetration Testing Services?
Expert Security Consultants
Our certified testers bring years of experience and utilize the latest tools to simulate real-world attacks on your systems.
01Comprehensive Reporting
We deliver detailed reports that highlight vulnerabilities, assess their impact, and provide actionable recommendations for remediation.
02Proven Methodology
By following industry-standard frameworks like OWASP, NIST, and PTES, we ensure our penetration tests are thorough and effective.
03Customized Solutions
We tailor our penetration tests to address your organization's unique needs and specific security concerns.
04Post-Test Support
We collaborate with your team to address vulnerabilities and provide guidance for maintaining a secure environment.
05Commitment to Confidentiality
We uphold strict confidentiality and ethical standards to ensure your sensitive information remains secure throughout the testing process.
06The best penetration testing recommendations

To maintain ongoing security, we suggest scheduling regular penetration tests—whether it’s annually, biannually, or quarterly. Cyber threats evolve constantly, and regular tests will help uncover new vulnerabilities before they can be exploited. This cycle-based approach ensures your systems remain resilient against both old and emerging threats. Furthermore, many compliance frameworks require routine security assessments, and adopting this approach helps you stay compliant while improving your overall security posture year-round.
Schedule Regular Penetration Testing Cycles 2
Integrating penetration testing into your SDLC identifies vulnerabilities early, minimizing security risks and reducing the cost of fixing issues later. This proactive approach ensures applications are built securely from the start, fostering a security-first mindset. By implementing security checks at key stages, you align with modern DevSecOps practices, ensuring continuous security integration throughout development.

After deploying critical updates or patches, it’s crucial to run penetration tests to ensure that these changes haven’t introduced new vulnerabilities. Often, patches that solve one problem may inadvertently create others. By conducting fresh tests after each update, you can verify that the fix has been applied correctly and that no new security gaps have been created. This approach is essential for maintaining the integrity of your systems, especially if they handle sensitive or regulated data.

We recommend combining automated tools with manual penetration testing to ensure comprehensive security coverage. While automated scans can quickly identify known vulnerabilities, manual testing by skilled experts can uncover more complex, hidden flaws that machines may miss. This hybrid approach allows for both broad and deep security assessments, helping to protect your systems against both common and sophisticated threats. Manual testing adds an extra layer of assurance by simulating real-world attacks in ways automated tools cannot.
Use Both Automated and Manual Testing Approaches 5
Industries We Serve
Financial Services
We provide security solutions to protect sensitive financial data, ensuring compliance with regulations like PCI-DSS. Our services help financial institutions defend against fraud, data breaches, and cyber threats.
Healthcare
We provide tailored security solutions for healthcare organizations, protecting patient data and medical records from breaches while ensuring compliance with HIPAA and other regulations, allowing providers to focus on patient care.
E-commerce
We protect e-commerce platforms from cyberattacks, securing payment gateways, customer accounts, and sensitive data. Our scalable solutions ensure full compliance with security standards for businesses of all sizes.
Government
Government organizations face major cyber threats, requiring strict security measures. We offer tailored solutions to protect data, ensure compliance with regulations, and defend against nation-state actors while maintaining services.
Manufacturing
As digital transformation impacts manufacturing, securing intellectual property and control systems is crucial. We provide tailored security solutions to protect operations, supply chains, and ensure business continuity.
Check Our Sample Penetration Testing Report
Web Penetration Testing Report

Network Penetration testing

Mobile Application Penetration Testing
Get Started Today
Don’t wait for an attacker to find the weak spots in your security. Our penetration testing services help you identify and fix vulnerabilities before they can be exploited. Contact us today to learn more about how we can help you secure your digital assets and ensure your business is protected from cyber threats.
Contact Us
to schedule a consultation and start securing your business today!
We recommend conducting penetration tests in a staging environment to prevent disruptions to live services. This setup mirrors production, allowing accurate results without risking downtime or data loss. Developers can safely identify and fix vulnerabilities, strengthening security before changes are pushed live. Testing in an isolated environment ensures safe improvements to your systems.
Perform Penetration Testing on a Staging Environment 1