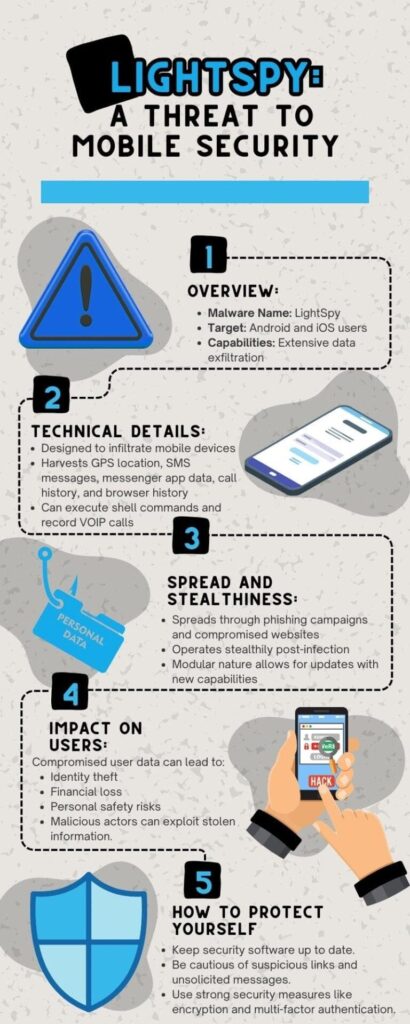
Recently, a sophisticated new threat, LightSpy Malware, has surfaced, posing a significant risk to Android and iOS users. With its advanced ability to extract sensitive user data, this covert surveillance tool has reverberated throughout the cybersecurity community. This article examines the technical complexities of LightSpy Malware, its operational methods, and its consequential impact on user privacy and security.
Exploring the Technical Aspects of LightSpy Malware
LightSpy is meticulously crafted to infiltrate mobile devices, exploiting vulnerabilities in both Android and iOS platforms. Its modular architecture enables it to execute a plethora of malicious activities, including but not limited to:
- GPS Location Tracking: LightSpy can surreptitiously harvest GPS location data, allowing malicious actors to track the victim’s movements with alarming accuracy.
- SMS and Messenger App Data Extraction: The malware indiscriminately intercepts SMS messages and data from popular messenger applications, potentially compromising sensitive conversations and personal information.
- Phone Call Surveillance: By clandestinely logging phone call history and recording voice-over IP (VOIP) call sessions, LightSpy breaches the sanctity of private communications.
- Browser History Monitoring: The malware clandestinely monitors the victim’s browsing activity, providing malicious actors with insights into their interests, habits, and online behavior.
Moreover, LightSpy can remotely execute shell commands, further augmenting its surveillance capabilities and facilitating unauthorized access to infected devices.

Propagation and Stealth Operations of LightSpy Malware
LightSpy employs various propagation techniques, including phishing campaigns and compromise of legitimate websites, to infect unsuspecting users’ devices. Once ensnared, the malware operates surreptitiously, often evading detection by leveraging its stealthy mechanisms.
Impact of LightSpy Malware on Users
The ramifications of a LightSpy infection are profound and far-reaching. The compromised user data can pave the way for identity theft and financial fraud and jeopardize personal safety. The real-time tracking of browser history and communications endows malicious actors with a treasure trove of exploitable information, exacerbating the risks manifold.
Mitigating Malware Risks
To mitigate the risk posed by LightSpy and similar malware, users are strongly advised to:
- Ensure their security software is up to date to detect and neutralize emerging threats.
- Exercise caution when encountering unsolicited communications or suspicious links that could serve as potential infection vectors.
- To fortify their digital defenses, adopt robust security measures, including encryption and multi-factor authentication.
Conclusion
The emergence of LightSpy underscores the ever-evolving threat landscape in the digital realm. Android and iOS users must remain vigilant and proactive in safeguarding their personal information against such sophisticated cyber threats. By staying abreast of the latest security protocols and exercising prudence in their online interactions, users can mitigate the risks of LightSpy and preserve their privacy and security in an increasingly interconnected world.
Source: https://gbhackers.com/lightspy-malware/
FAQ:
1. What is LightSpy malware, and why is it so dangerous?
LightSpy is a sophisticated malware that targets Android and iOS devices. It is designed to steal a wide range of sensitive user data, including GPS location, SMS messages, messenger app data, phone call history, and browser history. The malware can also remotely execute commands and record VOIP calls. This makes LightSpy a very dangerous threat to user privacy and security.
2. Apart from individual users, who else is at risk from LightSpy malware, and what are the potential consequences?
LightSpy malware poses significant risks to businesses, organizations, and society as a whole. Businesses face data breaches, financial losses, and operational disruptions. Organizations may experience sensitive data compromises, reputational damage, and public trust erosion. Society grapples with increased cybercrime, privacy concerns, and an evolving threat landscape.