Veeam Backup & Replication plays a pivotal role in safeguarding data across countless businesses, offering peace of mind with robust backup and recovery solutions. However, recent discoveries of severe vulnerabilities in Veeam Backup & Replication 12.1.2.172 and earlier versions underscore an urgent need for users to update and reinforce their backup security. In this article, we’ll break down these vulnerabilities, the risks they present, and how to protect your systems from potential attacks.
Overview of the Disclosed Vulnerabilities
Veeam’s internal testing revealed multiple vulnerabilities affecting Veeam Backup & Replication, each with the potential to compromise data security. These vulnerabilities range from allowing remote code execution (RCE) to enabling privilege escalation and bypassing Multi-Factor Authentication (MFA). With CVSS v3.1 severity scores ranging from high to critical, it’s clear these issues pose a substantial risk to unpatched systems.
Below, we delve into the details of each vulnerability and its potential impact.
In-Depth Look at Key Vulnerabilities
- CVE-2024-40711 – Critical Remote Code Execution (RCE) Vulnerability
This critical vulnerability, discovered by Florian Hauser with CODE WHITE GmbH, is one of the most severe. It allows unauthenticated attackers to execute remote code on affected systems. With a CVSS v3.1 severity score of 9.8, this vulnerability can lead to a complete system compromise, giving malicious actors full control over backup infrastructure and the ability to potentially alter, delete, or steal backup data.
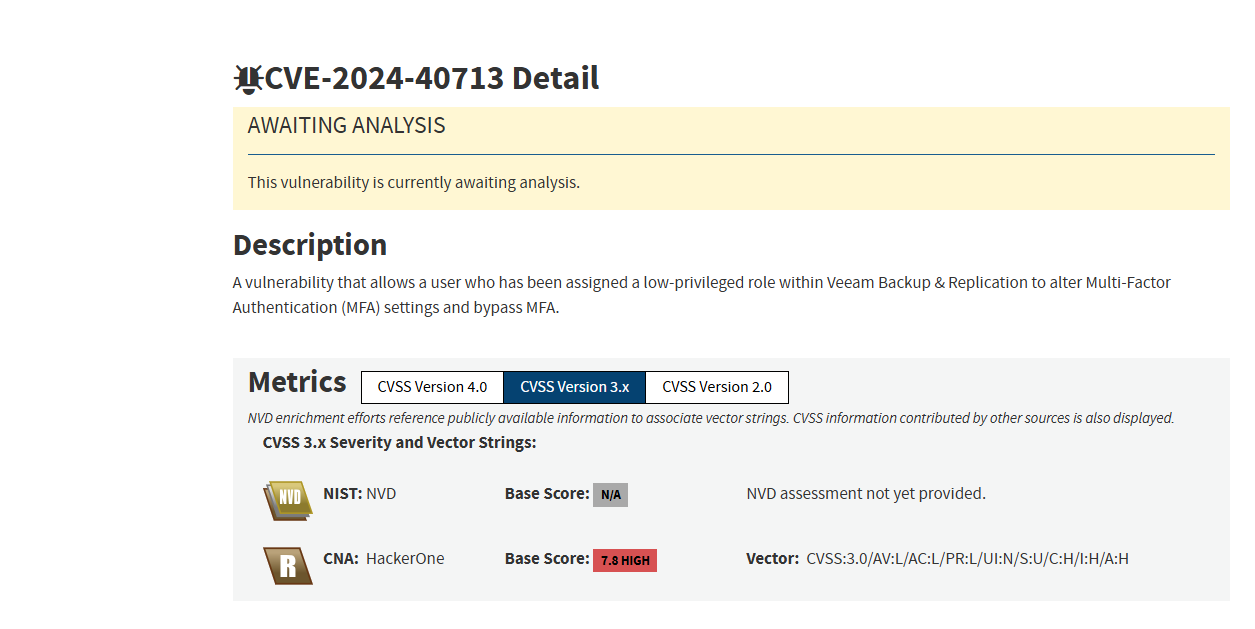
- CVE-2024-40713 – MFA Bypass Vulnerability
In another concerning flaw, users assigned low-privileged roles can modify and bypass Multi-Factor Authentication (MFA) settings. This vulnerability, rated with a CVSS v3.1 score of 8.8, allows low-privilege users to manipulate essential security settings, effectively negating the added layer of protection MFA provides. The risk here is significant, as it exposes critical accounts to unauthorized access.
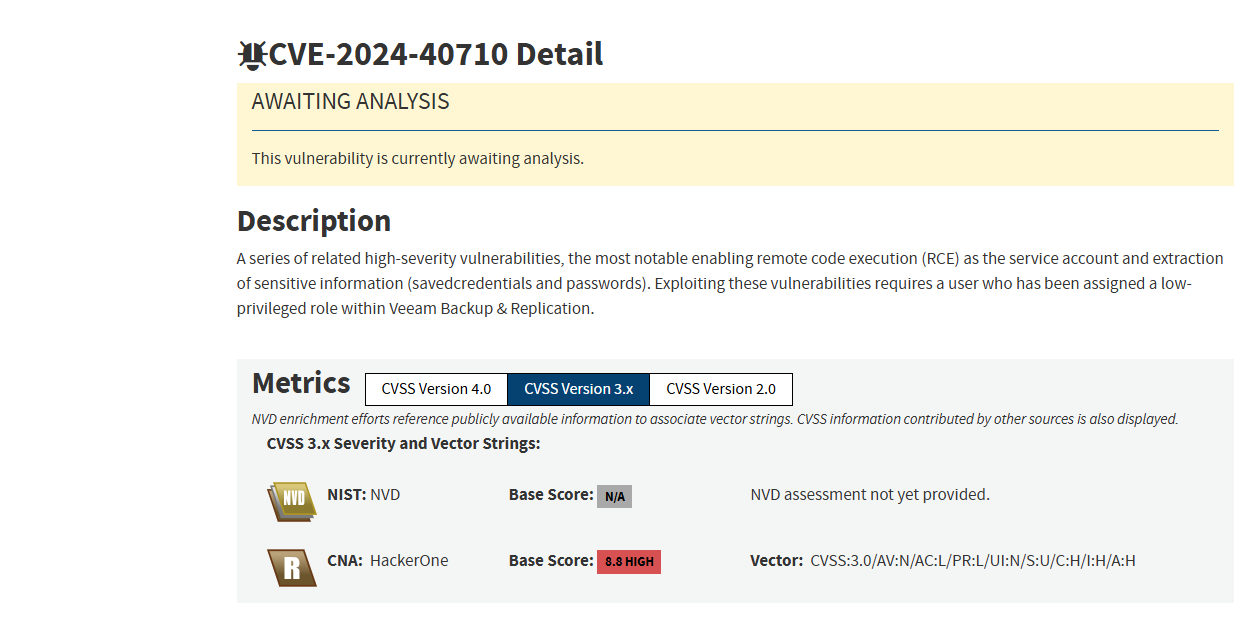
- CVE-2024-40710 – Remote Code Execution and Credential Extraction
This series of vulnerabilities enables remote code execution as the service account and the extraction of sensitive information, including saved credentials and passwords. Exploiting these vulnerabilities requires only low-privilege access, making it possible for attackers to gain unauthorized access and extract highly sensitive data. With a CVSS v3.1 score of 8.8, these vulnerabilities highlight the potential for far-reaching consequences.
- CVE-2024-39718 – Remote File Removal with Low-Privilege Access
Rated at 8.1 on the CVSS v3.1 scale, this vulnerability allows low-privileged users to remotely remove files with permissions equivalent to the service account. This vulnerability can lead to unintended data loss or sabotage, potentially disrupting critical business processes relying on Veeam Backup & Replication.
- CVE-2024-40714 – TLS Certificate Validation Flaw
This vulnerability in TLS certificate validation enables attackers on the same network to intercept sensitive credentials during restore operations. With a severity score of 8.3, this flaw poses a significant risk in environments where network security might be less stringent, as it allows attackers to access credentials and potentially compromise backup data during recovery.
- CVE-2024-40712 – Local Privilege Escalation (LPE) through Path Traversal
This path traversal vulnerability, rated at 7.8, allows attackers with low-privileged accounts to escalate their privileges on the local system, leading to an increased risk of full system compromise. Local privilege escalation vulnerabilities like this one are often used in conjunction with other exploits, making it easier for attackers to gain further access.
Solution and Mitigation
All the vulnerabilities listed above have been addressed in Veeam Backup & Replication 12.2 (build 12.2.0.334). If you are running an earlier version, updating to this latest version is crucial to ensure your backup environment remains secure.
Additionally, following best practices for cybersecurity in backup infrastructure is essential. Here are some proactive steps you can take:
- Regular Updates: Ensure all software is up-to-date to protect against known vulnerabilities.
- Least Privilege Access: Limit user permissions to the minimum required to reduce the risk of exploitation.
- Network Security: Isolate your backup infrastructure from public networks where possible to minimize exposure.
- MFA Reinforcement: Regularly review MFA settings and roles within the backup system to identify any potential misconfigurations.
Importance of Staying Updated
Cybersecurity is a constantly evolving landscape, and backup solutions are not immune to vulnerabilities. Staying updated with the latest patches and security disclosures is essential in safeguarding sensitive data. Regular patching ensures vulnerabilities like those discussed in this article cannot be exploited by malicious actors, keeping your systems and data safe.
Conclusion
The recent vulnerabilities discovered in Veeam Backup & Replication emphasize the importance of maintaining a secure, updated backup environment. With the potential for unauthorized access, data loss, and credential compromise, it’s clear that immediate action is necessary for users of affected versions. Updating to Veeam Backup & Replication 12.2 and following best practices in backup security will help mitigate these risks and protect your organization from potential threats.
